Being attacked by hackers on the DeFi protocol is something that no user or developer wants to encounter, but this risk is always present anywhere. So what should we do when the DeFi protocol we used is hacked? Or join Weakhand to find out in this article.
Types of Attacks Commonly Used by Hackers
Attack smart contracts
It can be said that smart contracts are the backbone of DeFi protocols as they hold the operating rules of any action. However, it is inevitable that programmers will miss errors while writing their smart contracts.
Hackers will take advantage of these vulnerabilities to perform a smart contract attack and steal the assets contained therein. Hackers can even steal assets in user wallets if they previously approved smartcontact to use a large number of tokens.
Because the DeFi market cannot operate without smart contracts, the frequency of smart contract attacks is also very high with the total damage to date reaching billions of dollars in just a few years. .
Wormhole Exploited is probably one of the largest smart contract related attacks in the DeFi market as a total of over 120K WETH was stolen in this event, which at the time of the incident was worth over $360 M. The entire stolen amount has been recovered and compensated to users, but this is a red flag for the security and auditing of smart contracts in DeFi.
Wormhole Hack Thread 🧵 Additional Details + Prevention
Others have already described how it happened, going to talk about how it could have been prevented and note additional details that haven’t been covered.
— wireless (@wireless_anon) February 3, 2022
Attack Oracle
If smart contracts are said to be the backbone of the market, Oracles will be the nervous system created with the purpose of transmitting price information between the real world and DeFi. All current Oracles are transmitting information of about $35B in assets, accounting for 67% of the total TVL of the DeFi market.
To carry out the process of transmitting information accurately and quickly, Oracles will build a network consisting of many different Nodes. Node operators are usually reputable parties who will be carefully selected and must go through a strict KYC process to ensure there is no fraud in the process.
However, Oracles often have certain problems when the market fluctuates, causing the prices of many tokens to change continuously. This causes the recorded price and the price transmitted to different DeFi protocols, arbitrage bots will now take advantage of this flaw to buy where the price is low and sell where the price is high for the purpose of profit however it will cause damage to the protocol users.
One of the most famous Oracle-related attacks occurred on BonqDAO with about $120 in assets stolen by hackers. The attackers took advantage of a vulnerability in Oracle’s updatePrice function to manipulate the price and then withdraw wABLT and BEUR and sell them for USDC along with ETH.
The @BonqDAO is exploited and its price oracle is manipulated to increase the #WALBT price. price. Here is the example hack tx: pic.twitter.com/XrzExHY6m1
— PeckShield Inc. (@peckshield) February 1, 2023
Attack Front running
Front-running is a form of attack based on the ability to know in advance that a certain transaction will cause price fluctuations. This term has been around for a long time in the traditional market when those who have news about someone else will buy a large number of stock codes, causing the price to increase sharply, the job of the person with the news is just to buy before that transaction occurs and sell immediately afterward to profit from the difference.
Most Blockchains, especially Ethereum, use a model called Mempool, which is where transactions will be contained before being included in the Block by Validators and attached to the Blockchain. The disadvantage of this model is that Validators will prioritize arranging transactions that pay more fees into the Block first, making Front-run transactions easier to take place with bots.
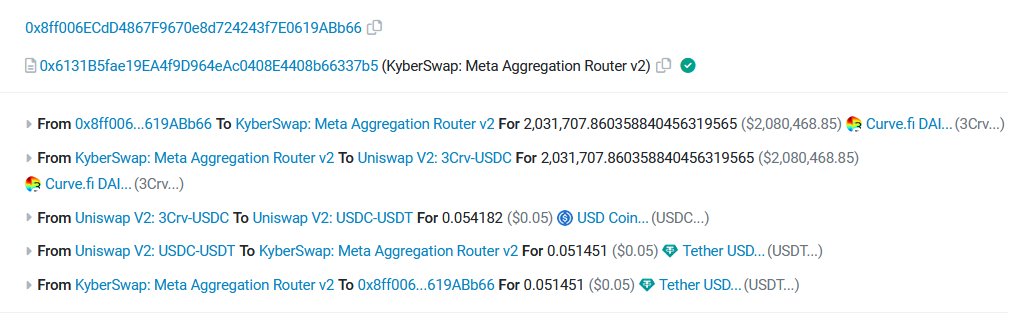
One of the most typical examples for Front-running is the case of a user on KyberSwap who swapped $2M but only recovered 0.05 USDT for that transaction. Specifically, at that time, on March 11, 2023, stablecoin USDC was affected after SVB bank collapsed, causing the price to lose more than 10%.
The above user may have panicked or for some reason sold more than $2M of 3CRV tokens in exchange for stablecoin USDT. 3CRV is the token representing the DAI-USDC-USDT liquidity of Curve Finance users. Due to the decrease in USDC price, the value of the remaining 2 stablecoins was also affected, so they were forced to withdraw it from the pool.
Normally, people need to access Curve Finance to withdraw their money instead of swapping it somewhere, but the above user did not do that and instead brought his 3CRV tokens to sell through KyberSwap. KyberSwap’s router found a dead liquidity pool on Uniswap with only about 2 USDC available liquidity then sold $2M 3CRV in exchange for 0.054 USDC and then continued to swap to 0.05 USDT to return to the user.
A MEV bot discovered the above transaction’s anomaly and provided 1.4 USDC liquidity to the pool on Uniswap then withdrew it to $2M 3CRV. The fee that MEV bot paid to the network was 23.7 ETH, equivalent to $39K at that time to ensure the transaction occurred.
Flash Loan attack
The term Flash Loan was born in 2020 by AAVE as a feature that allows users to borrow money without collateral but must repay the borrowed amount in the same transaction block. This feature allows borrowers to make quick profits with arbitrage or Yield Farming transactions in a snap and lenders can also earn a larger fee.
Other Lending & Borrowing platforms also realize the potential of this feature so they have learned and developed it to integrate into their products. However, security problems also started to arise from here when they did not have a thorough audit of their Flash Loan product.
Flash Loan attacks often occur based on common errors in the protocol:
- Flash Loan Slippage Attack
- Flash Loan Price Oracle Attack
- Flash Loan Swap Logic Exploit
- Flash Loan Reentrancy Attack
Attacking Front-ends
Front-ends attack is a form in which hackers take advantage of holes in the user interface on project websites to install malicious code. Users who click on these malicious codes will be redirected to a phishing website or have to sign malicious transactions on the Metamask wallet.
This form of attack occurs quite frequently in the DeFi market, with an average of one attack per month:
- Balancer Front-ends: The attack occurred on September 19, 2023 and hackers stole a total of $238K from users.
- Galxe Front-ends: This attack occurred on October 6, 2023 and a total of over $100K in damage occurred, the Galxe attacker used the same wallet address as the Balancer attack.
- Velo Front-ends: 2 projects with the same development team, Veldrome and Aerodrome, were attacked on the same Front-ends on November 29, 2023 and then attacked again on December 2, 2023 with The amount of damage has not been calculated.
What to Do When the DeFi Protocol You Used Was Hacked?
Determine in what form the protocol is being attacked
As mentioned above, there are many different methods to attack a DeFi protocol, so to come up with the best solution, the first thing everyone needs to do is determine the method. where the project is attacked.
In addition to determining in what form the protocol was attacked, people also need to determine whether their liquidity pool providing liquidity is one of the attacked pools or not.
Necessary actions
If people regularly participate in providing liquidity in DeFi through Yield Farming or depositing money in Lending & Borrowing protocols, Front-ends or Front running attacks will not cause any damage. What everyone needs to do at this point is to keep their assets intact and not interact with the protocol until there is information that it is safe to use again.
For the remaining forms of attack, everyone needs to immediately withdraw their assets from the protocol if the liquidity pool of the assets being deposited is not affected. To be able to withdraw money smoothly, people need to adjust their gas fees many times higher than at that time.
If your assets are in the affected liquidity pools, then you need to try to withdraw assets if possible through the platform’s main transaction or through smart contracts (withdrawing via smart contracts will need to be converted in many ways). The units of measurement are different, so people can rely on the help of AIs like ChatGPT to convert). If you have tried everything but cannot withdraw money, you need to immediately contact the project team via Discord to receive support.
Prevention is better than cure
The saying that prevention is better than cure is not only true in medicine, but it is also true when people participate in skin in the game in the DeFi market. Being prepared will help people avoid hackers looking at their assets with the following methods:
- Do not approve more than the usage amount: Normally, before depositing assets into any protocol, people will have to go through an operation to grant rights to use the assets. By default, people usually give unlimited rights to use that token in their wallet, so if smart contracts are attacked, hackers can easily withdraw money from the victim’s wallet.
- Split trading volume: If people trade an amount of a few hundred to a few thousand dollars in a liquidity pool of hundreds to millions of dollars, there is no problem, however if people trade an amount from a few hundred thousand to even million dollars, the price slippage will be very high and MEV bot will take advantage of it to attack easily. Therefore, breaking an initial transaction into multiple transactions will help people avoid Front running.
- Be careful when signing a transaction: Metamask also has special warnings for suspicious transactions, so before signing any transaction, everyone should read through the content of that transaction.
- Subdivide assets: Asset splitting will be at two different levels: wallet and protocol. First, people need to divide large and small assets into each wallet depending on the risk level, then distribute assets to many different protocols with the same purpose of use.
Summary
Above are the most common forms of attacks today in the DeFi market. Weakhand hopes that through this article, everyone will know what they should do when the DeFi protocol they used is hacked.


