In this article we will learn together the term Protocol, this term is often associated with the names of many projects and is a very important term in the field of Cryptography and Blockchain.
What is Protocol?
The term Protocol can be interpreted in many different contexts, but at a basic level, Protocol is often understood as a set of rules and procedures designed to regulate, direct, or manage activities. between different entities, including computer systems and network-connected devices.
Specifically, in computer networks, Protocol is used to ensure communication between devices is synchronized, has a standard format, and ensures data integrity. Many different protocols are used in the field of computer networking, including network protocols such as TCP/IP, HTTP, DNS, SMTP, FTP, and SSH.
In the Crypto field, Protocol is often used to refer to mechanisms and processes designed to protect information and ensure the integrity of the blockchain system, in which information and transactions are encrypted with encryption keys. cryptographic algorithm. Popular protocols in Crypto include Bitcoin Protocol, Ethereum Protocol, zk-SNARKs Protocol,…
In short, the term Protocol can be explained as a set of rules and procedures designed to regulate, direct, or manage activities between different entities, depending on the context of use of each. field.
Structure Of Protocol

A Protocol consists of rules and procedures designed to regulate, direct and manage activities between different entities. A Protocol can include the following components:
- Rules: Act as guidelines and directives, produced by Protocol designers. Rules aim at a specific purpose, for example, describing how to create connections, establish and maintain connections, format data, handle errors, and more.
- Messages: Messages are conveyed between entities to perform operations specified by Protocol rules.
- Control mechanisms: data flow control, error control, ensuring data integrity and data security or encryption.
- Association Protocol: Governs how entities connect and disconnect.
- Routing protocol: Governs how messages are forwarded across the network from one location to another.
- Application protocols: Protocols designed to meet the needs of specific applications, such as the SMTP protocol for email.
Depending on the purpose and application of the Protocol, it may have one or more of the above components and may use many different protocols to work together.

The structure of a Protocol includes components that are often organized in a specific structure to help manage and control messages, data, and operations between different entities on the network. The main components of the Protocol structure include:
- Header: Is the first part of the data of a message sent in the protocol. It contains important information such as the source and destination addresses of the message, data format, length and sequence number of the message.
- Payload: This is the part that contains the actual content of the message in the protocol. Payloads can contain information such as strings of characters, numbers, files, or any other type of data formatted by the protocol’s rules.
- Footer: As the last part of a message in a protocol, the footer often contains a checksum or digital signature to ensure that the message is transmitted to the correct address without error or tampering.
- Command/Opcode: Used in protocols to send requests or instructions to perform an action such as add, edit, delete, retrieve and more between different computers or devices on the network.
- Error codes: Error codes are used in the protocol to report errors that occur during communication between different entities. Error codes help systems and applications handle errors quickly and effectively.
Depending on the purpose and nature of the protocol, the structure may vary, but the above components are usually the basic parts of a common Protocol.
Protocols play an important role in the structure of a Blockchain network. However, we must distinguish between the Protocol of the Blockchain network and the Layer Protocols (layer protocols) of the network on which the Blockchain is built.
The Blockchain network can be viewed as a hierarchical structure (such as the OSI model) consisting of different layers. These layers (layers) often include:
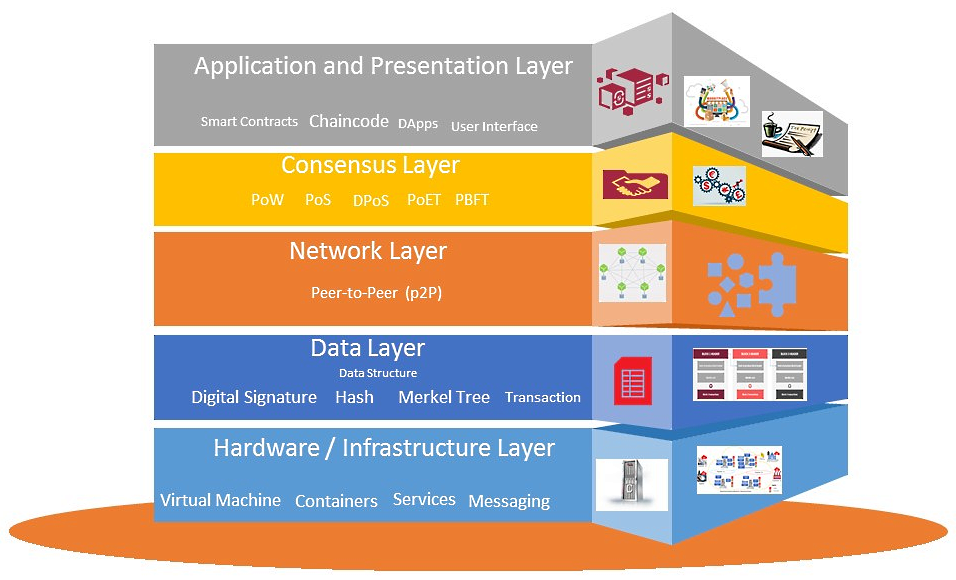
- Application layer: This layer plays an important role in determining the applications and protocols that will be used on the Blockchain network. For example, Bitcoin and Ethereum are two popular applications built on Blockchain networks.
- Network layer: This layer includes protocols that link nodes in the Blockchain network together, allowing transactions and information to be transmitted and received on the network.
- Consensus layer: This layer ensures that nodes in the Blockchain network agree on the exact state of the system using consensus protocols such as Proof of Work, Proof of Stake, or other consensus protocols.
- Protocol layer: This layer contains the protocols that the Blockchain network uses to ensure the integrity and security of information and transactions. These protocols include Bitcoin Protocol, Ethereum Protocol, zk-SNARKs Protocol, and many others.
Therefore, Protocol is located at the lowest layer of the Blockchain network structure. However, these protocols are the most important components of the Blockchain system because they ensure the integrity and security of information and transactions on the network.
Mechanism of Operation of the Protocol
The operating mechanism of a Protocol is built to control, manage and monitor activities between different entities on a network. A protocol typically works according to the following steps:
- Establishing a connection: One entity sends a connection request to another entity on the network. Once the request is received, the entity responds to the request by establishing a connection.
- Authentication: Once a connection is established, entities authenticate and check each other’s identities to ensure that information and transactions are transmitted and received to the right place and recipient.
- Sending and receiving messages: Once connection and authentication are established, entities can transmit information and transactions to each other using messages formatted according to the protocol’s rules.
- Message Processing: Entities that receive a message process it using the corresponding protocol’s rules to check the integrity, reliability, and authenticity of the information.
- Transaction completion: Once the entities have confirmed the information and transaction, the protocols complete the transaction and release the connection.
In addition, protocols include mechanisms to control data flow, control errors, ensure data integrity, and secure or encrypt data to ensure that information and transactions on the network are protected and protected. safe. Depending on the purpose and nature of the protocol, its rules and procedures may vary.
Some Applications of Protocol

Protocol is a concept that is widely used in many different fields and has many different applications. Here are some applications of Protocol:
- Computer network: Network protocols such as TCP/IP, DNS, HTTP are used to format, manage and manage activities between network-connected devices.
- Crypto: Crypto protocols such as Bitcoin Protocol, Ethereum Protocol, zk-SNARKs Protocol are used to ensure the integrity and security of information and transactions on the Blockchain network.
- Robotics: ROS (Robot Operating System) protocol is used in programming and operating Robot systems.
- Communications and Telecommunications: PSTN network protocols, such as SIP (Session Initiation Protocol) are used to control and manage calls between phones or other communication devices.
- Internet of Things (IoT): IoT protocols such as MQTT, CoAP, Zigbee, Z-Wave are used to connect and manage IoT devices, collect data and control devices.
- Game: Game network protocols such as UDP (User Datagram Protocol), TCP (Transmission Control Protocol), SCTP (Stream Control Transmission Protocol) are used to manage and format information needed for online game activities .
- Cloud computing: Data access and management protocols in cloud computing systems such as REST API, SOAP are used to access and manage resources in cloud computing service systems .
- Network security: Network protocols such as SSH (Secure Shell), SSL (Secure Socket Layer), TLS (Transport Layer Security) are used to ensure the security of information transmitted over the network and user authentication.
In short, Protocol has many different applications in many different fields, from computer networks, Crypto to IoT, cloud computing and network security.
Compare Protocols With dApps
|
|
Protocol |
dApp |
|---|---|---|
|
Define |
Rules and procedures are designed to regulate, direct and manage activities between different entities. |
Applications developed on the blockchain platform are often distributed and not centralized. |
|
Purpose |
Ensure the integrity, safety and security of information and transactions online. |
Provide distributed platform services or applications on blockchain that can be used for different purposes such as finance, insurance, business and more. |
|
The components |
Includes rules, data formats, protocol codes, and control mechanisms. |
Decentralization stands out because the dApp is developed on a blockchain platform, with the aim of creating a completely decentralized environment. |
|
Dispersion |
Can be distributed or non-distributed depending on the purpose of the protocol. |
Decentralization stands out because the dApp is developed on a blockchain platform, with the aim of creating a completely decentralized environment. |
|
Data management |
Can manage and deliver data on a different network through protocols. |
Usually a distributed log system is used, where everyone has access to a copy of the log, and the log is not dependent on any one version of it. |
Summary
So I have clarified what Protocol is? And clarify the difference between Protocol and dApp. Hope this article brings a lot of useful knowledge!


