We have heard a lot about Validity Proofs as well as Fraud Proofs. So what is the difference between them? Let’s learn in detail about these two types of evidence below!
Introduce
In this article, we will analyze and compare different Layer 2 (L2) scalability solutions, based on the difference between Validity Proofs and Fraud Proofs. ). In our opinion, Validity Proofs have a fundamental advantage, in that they guarantee that nothing other than the correct state transition is accepted.
Basics of Validity Proofs and Fraud Proofs
In recent times, many solutions to solve Ethereum’s scalability problem have appeared such as projects: Truebit, Gluon Plasma, dFusion, Roll-Up and Ignis. Basically, the idea is quite simple: instead of writing many transactions to the blockchain, they create a short proof (e.g., hash) of these transactions that represents the new state of work .
The projects mentioned above are all L2 solutions: they define a protocol (and logic) that runs on Layer 1 (L1) and rely on it for implementations for different services: deposits/withdrawals , the ledger for off-chain state commitments, giving them the appearance of a “multimeter”. Importantly, L1 is not aware of, and therefore cannot execute, any of L2’s logic.
We will focus on the differences between Validity Proofs and Fraud Proofs based on a framework to compare them. Essentially, Validity Proofs and Fraud Proofs can still exist in L1, but now our divisions will take place on L2.
Fraud Proofs present evidence that state transitions are incorrect. They will assume that the blocks simply represent the exact state of the L2 data, until proven otherwise. In practice, a committed block may also include an incorrect state transition.
Validity Proofs provide evidence that the state transition is correct. Blocks include values that represent L2 state if and only if that state is correct.
Before continuing, we need to emphasize that: Proof systems (e.g. SNARK, STARK) can be used as Validity Proofs and Fraud Proofs. People should not confuse the two How we use proof (e.g. SNARK, STARK) with what we will demonstrate (Fraud or Validity).
Validity Proofs Vs. Fraud Proofs: Key Differences
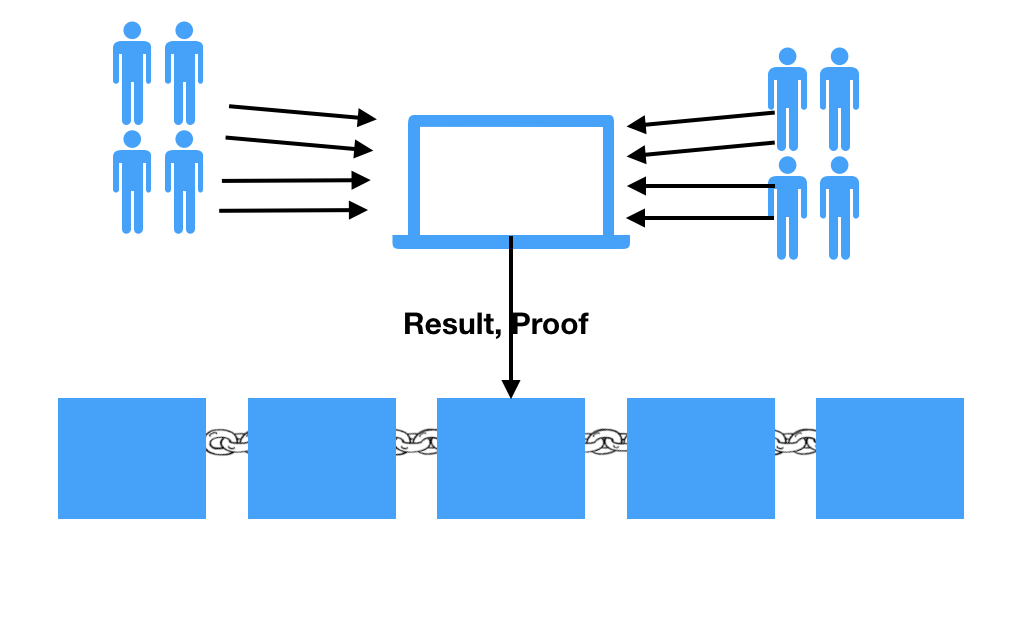
Fraud Proofs
The main advantage of Fraud Proofs is that they are not needed for every state transition, but only when things are believed to be incorrect. Therefore, they require fewer computational resources and are more suitable for environments with limited scalability.
The main disadvantage of these protocols stems from their interoperability: they define a ‘conversation’ between multiple parties. A chat requires parties – especially the party claiming fraud – to be present (and active) and allows other parties to interrupt the conversation in a variety of ways.
But the heart of the matter is the protocol’s interpretation of silence (no challenge to a new state) as tacit consent. Accordingly, the attacker may try to create a semblance of silence with DDoS attacks.
We will briefly describe the conceptual protocol: Since a block can include imprecise state transitions, the Fraud Proofs protocol allows a time frame – Time Delay dispute (Dispute Time Delay/DTD) – to dispute this incorrect state.
If no Fraud Proofs are sent in the DTD, the L2 state transition is considered correct. If the Fraud Proofs are sent to the smart contract and are determined to be correct (i.e., were sent in the DTD and actually proved the state transition was incorrect), then it will at least result in a contract. intelligently return to the commitment of the last correct L2 state. Additional steps, such as penalties for the offending party, may be imposed.
The choice of DTD duration is a consequence: the longer the duration, the more likely it is to detect incorrect state transitions – the better it is. However, the longer the time, such as the user having to wait longer to withdraw money, is not good at all.
Validity Proofs
Validity Proofs are representative proofs of some off-chain computation sent to a smart contract. The smart contract only updates the blockchain with this new value once it has been verified as correct.
The main advantage of Validity Proofs is that the blockchain will always reflect the correct L2 state and new state can be injected and used immediately. As for the downside, Validity Proofs requires proof for every state transition and this affects the scalability of the platform.
51%-Attacks
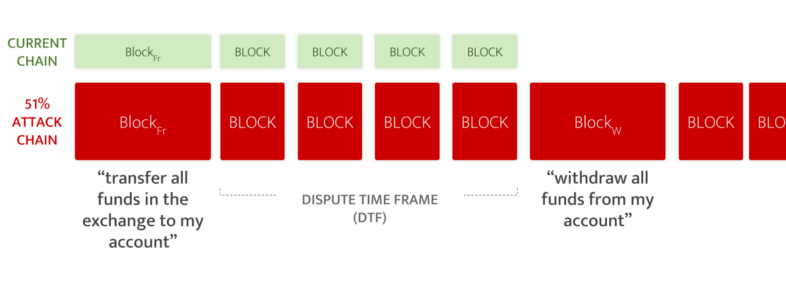
Among the many possible attacks, we want to focus on 51%-Attacks on L1. Recently, we have seen a spike in these attacks, including the attack on Ethereum Classic. How can Validity Proofs and Fraud Proofs defend against similar attacks?
Fraud Proofs: A 51%-attack allows an attacker to inject a fraudulent state into the blockchain and then steal funds from the exchange being attacked. We will learn more details below:
In short, the core issue is that the L2 solution defines its own logic and specifically allows a block containing a cheating state transition. The state of the ledger after the attacker steals the funds is the legitimate state!
Validity Proofs: A 51%-attack can destroy the recorded transaction history and can provide an alternative history; importantly, this alternative history is also valid. The range of attacks that can be performed is limited to L1. In crypto-to-crypto exchanges (especially, when all the assets being traded are on the same blockchain), dumping recorded history can sometimes be an extreme move. profitable: for example, a seller may be happy to cancel a transaction that took place at a lower price than expected.
Proposed Solutions
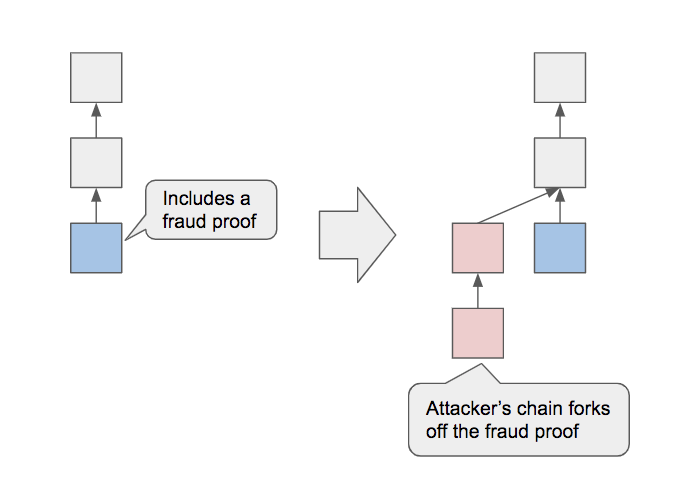
Why are Fraud Proof systems (e.g. Gluon Plasma and dFusion) being considered, given these significant disadvantages? Actually, the main reason is that proving validity is too expensive and cumbersome in recent times.
Before using Proof Systems, scalability was very limited. Proof Systems offer a very attractive characteristic called brevity: to validate a state transition, one only needs to verify a proof, and this is done at a very low cost, completely does not depend on the scale of the state transition.
Meanwhile, SNARK-based Ignis/Roll-Up requires significantly more reliable setups and computing resources to prove than STARK. StarkWare is working on implementing StarkDEX, its scalability solution for DEX, and will use STARK to achieve Validity Proofs.
Summary
Together we learned about Validity Proofs and Fraud Proofs as solutions to increase scalability on L2. The most powerful advantage of Validity Proofs is its ability to deal with 51% attacks. And now STARK, with its fast proof time, short verification, and trustless setup, is an attractive means of generating Validity Proofs. Let’s wait and see if StarkWare achieves those big goals with Validity Proofs in the near future!


